What Is Confidential Computing? | NVIDIA Blogs

Cloud and edge networks are placing up a new line of protection, identified as confidential computing, to protect the expanding prosperity of details people approach in those environments.
Private Computing Defined
Confidential computing is a way of shielding data in use, for example although in memory or throughout computation, and avoiding any one from viewing or altering the perform.
Making use of cryptographic keys linked to the processors, confidential computing makes a reliable execution surroundings or secure enclave. That harmless electronic place supports a cryptographically signed proof, named attestation, that the hardware and firmware is properly configured to stop the viewing or alteration of their data or software code.
In the language of protection specialists, confidential computing gives assurances of knowledge and code privateness as well as information and code integrity.
What Can make Private Computing Exclusive?
Private computing is a reasonably new capability for defending info in use.
For several yrs, personal computers have utilized encryption to secure data that’s in transit on a network and details at relaxation, stored in a drive or non-volatile memory chip. But with no useful way to run calculations on encrypted info, users confronted a hazard of owning their facts viewed, scrambled or stolen when it was in use within a processor or main memory.
With private computing, methods can now include all three legs of the details-lifecycle stool, so information is in no way in the obvious.
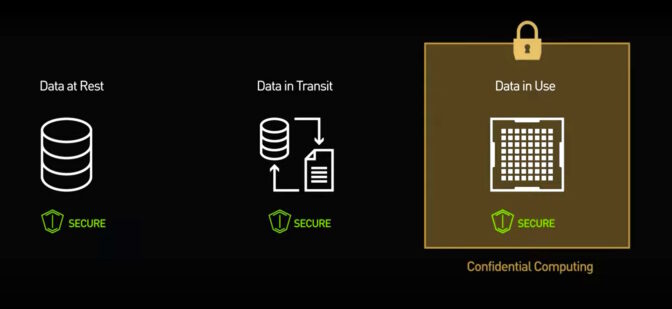
In the past, computer system safety primarily centered on protecting facts on programs customers owned, like their company servers. In this situation, it’s all right that system software sees the user’s data and code.
With the advent of cloud and edge computing, customers now routinely operate their workloads on desktops they don’t own. So private computing flips the focus to protecting the users’ data from whoever owns the equipment.
With private computing, software jogging on the cloud or edge laptop or computer, like an running procedure or hypervisor, still manages function. For example, it allocates memory to the person application, but it can under no circumstances read or alter the info in memory allocated by the user.
How Private Computing Received Its Name
A 2015 investigation paper was one of many applying new Safety Guard Extensions (Intel SGX) in x86 CPUs to display what is possible. It identified as its technique VC3, for Verifiable Confidential Cloud Computing, and the identify — or at the very least element of it — trapped.
“We started out calling it confidential cloud computing,” claimed Felix Schuster, direct author on the 2015 paper.
Four many years later, Schuster co-established Edgeless Devices, a firm in Bochum, Germany, that develops resources so users can make their individual confidential-computing apps to increase data defense.
Confidential computing is “like attaching a deal to your details that only allows specific matters to be finished with it,” he said.
How Does Private Computing Perform?
Taking a deeper look, private computing sits on a foundation referred to as a root of trust, which is primarily based on a secured crucial distinctive to each and every processor.
The processor checks it has the proper firmware to get started working with what is named a safe, calculated boot. That course of action spawns reference information, verifying the chip is in a acknowledged risk-free condition to commence work.
Up coming, the processor establishes a safe enclave or dependable execution surroundings (TEE) sealed off from the rest of the process where the user’s application runs. The application brings encrypted information into the TEE, decrypts it, operates the user’s application, encrypts the outcome and sends it off.
At no time could the device proprietor perspective the user’s code or information.
A single other piece is important: It proves to the consumer no one particular could tamper with the knowledge or program.
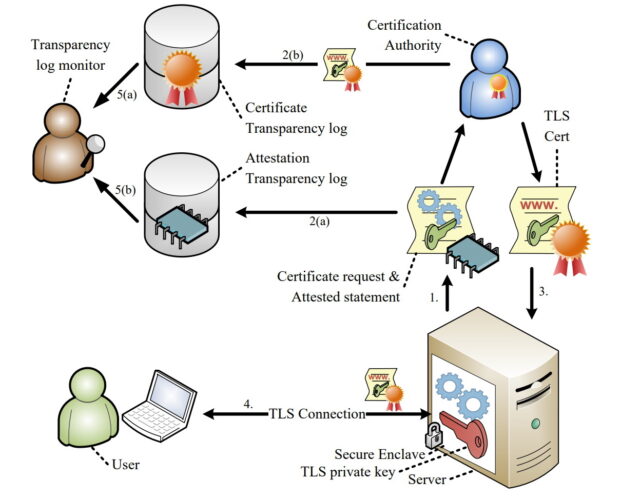
The proof is shipped via a multi-stage procedure termed attestation (see diagram over).
The very good news is researchers and commercially offered companies have demonstrated confidential computing is effective, usually furnishing info safety without substantially impacting overall performance.
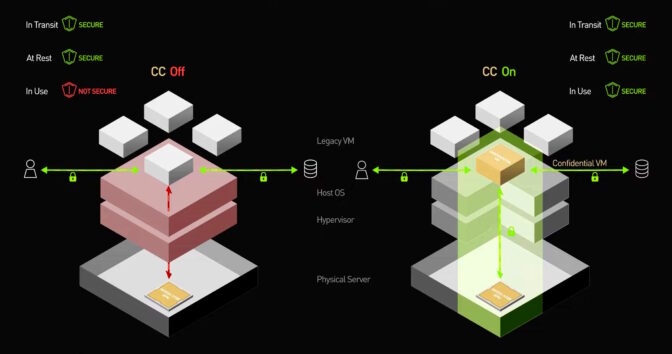
Shrinking the Safety Perimeters
As a final result, consumers no more time have to have to rely on all the application and techniques administrators in separate cloud and edge companies at remote destinations.
Private computing closes numerous doors hackers like to use. It isolates systems and their facts from attacks that could appear from firmware, working programs, hypervisors, virtual machines — even bodily interfaces like a USB port or PCI Categorical connector on the laptop or computer.
The new stage of safety guarantees to lessen knowledge breaches that rose from 662 in 2010 to extra than 1,000 by 2021 in the U.S. by yourself, according to a report from the Id Theft Source Center.
That reported, no stability measure is a panacea, but private computing is a wonderful stability instrument, placing command straight in the hands of “data owners”.
Use Scenarios for Confidential Computing
Consumers with sensitive datasets and regulated industries like banks, healthcare providers and governments are between the to start with to use confidential computing. But that’s just the start.
Because it protects delicate facts and mental home, confidential computing will enable teams truly feel they can collaborate properly. They share an attested proof their content material and code was secured.
Illustration programs for confidential computing involve:
- Businesses executing intelligent contracts with blockchains
- Investigation hospitals collaborating to teach AI versions that examine developments in individual information
- Shops, telecom suppliers and other folks at the network’s edge, defending private details in places the place physical obtain to the computer is attainable
- Software package vendors can distribute products and solutions which contain AI products and proprietary algorithms when preserving their mental property
Even though private computing is finding its commence in public cloud expert services, it will unfold rapidly.
Users will need confidential computing to safeguard edge servers in unattended or challenging-to-reach areas. Business knowledge centers can use it to guard against insider attacks and guard one private workload from a further.
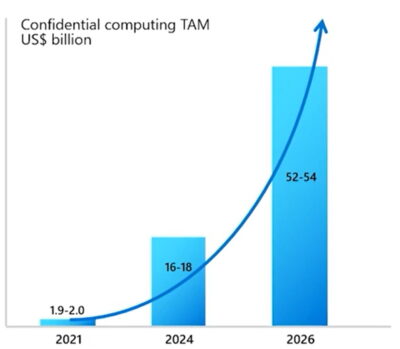
So significantly, most end users are in a evidence-of-principle stage with hopes of placing workloads into output quickly, said Schuster.
On the lookout ahead, private computing will not be minimal to unique-goal or sensitive workloads. It will be applied broadly, like the cloud services hosting this new stage of security.
In truth, experts predict confidential computing will develop into as widely utilised as encryption.
The technology’s prospective motivated suppliers in 2019 to start the Confidential Computing Consortium, section of the Linux Basis. CCC’s members consist of processor and cloud leaders as perfectly as dozens of program organizations.
The group’s tasks include the Open Enclave SDK, a framework for setting up dependable execution environments.
“Our most important mandate is supporting all the open-source initiatives that are foundational sections of the ecosystem,” explained Jethro Beekman, a member of the CCC’s technological advisory council and vice president of technological know-how at Fortanix, 1 of the very first startups started to produce confidential computing computer software.
“It’s a powerful paradigm to set protection at the facts level, fairly than get worried about the particulars of the infrastructure — that need to final result in not needing to examine about facts breaches in the paper just about every working day,” mentioned Beekman, who wrote his 2016 Ph.D. dissertation on confidential computing.
How Confidential Computing Is Evolving
Implementations of confidential computing are evolving rapidly.
At the CPU stage, AMD has launched Secure Encrypted Virtualization with Safe Nested Paging (SEV-SNP). It extends the course of action-stage protection in Intel SGX to complete digital machines, so consumers can employ confidential computing with no needing to rewrite their programs.
Top rated processor makers have aligned on supporting this tactic. Intel’s help comes through new Trusted Area Extensions. Arm has explained its implementation, known as Realms.
Proponents of the RISC-V processor architecture are utilizing confidential computing in an open up-source task called Keystone.
Accelerating Confidential Computing
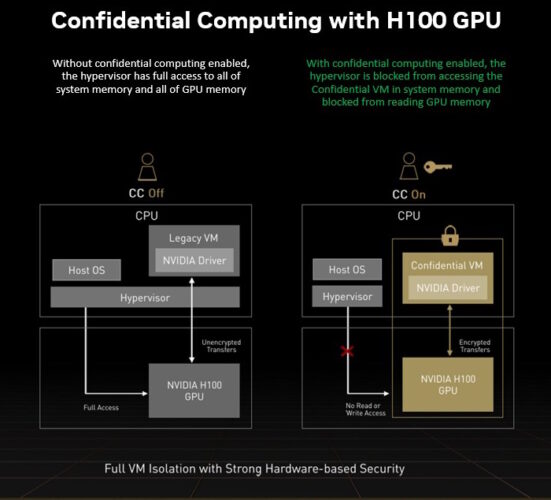
NVIDIA is bringing GPU acceleration to VM-style private computing to market place with its Hopper architecture GPUs.
The H100 Tensor Main GPUs enable confidential computing for a wide swath of AI and significant effectiveness computing use cases. This gives users of these safety services entry to accelerated computing.
In the meantime, cloud service providers are presenting services today dependent on one particular or more of the underlying technologies or their possess special hybrids.
What’s Up coming for Private Computing
More than time, industry suggestions and expectations will arise and evolve for features of private computing such as attestation and productive, protected I/O, explained Beekman of CCC.
Whilst it is a reasonably new privacy software, private computing’s ability to shield code and info and deliver assures of confidentiality makes it a highly effective one.
Hunting forward, experts anticipate private computing will be blended with other privacy solutions like fully homomorphic encryption (FHE), federated learning, differential privateness, and other types of multiparty computing.
Using all the elements of the modern-day privacy toolbox will be key to success as need for AI and privateness grows.
So, there are numerous moves forward in the great chess match of stability to defeat the difficulties and know the positive aspects of private computing.
Choose a Deeper Dive
To understand additional, look at “Hopper Confidential Computing: How it Performs Under the Hood,” session S51709 at GTC on March 22 or later on (absolutely free with registration).
Check out out “Confidential Computing: The Developer’s Look at to Protected an Application and Details on NVIDIA H100,” session S51684 on March 23 or later on.
You also can attend a March 15 panel dialogue at the Open up Private Computing Conference moderated by Schuster and showcasing Ian Buck, NVIDIA’s vice president of hyperscale and HPC. And watch the online video under.
:max_bytes(150000):strip_icc()/GettyImages-1436814898-536d5de45fd548688fbc829016728f70.jpg)






